While monitoring the latest Threat Intelligence and InfoSec news articles I came across an excellent article posted on April 17th, 2018 by the company “AdGuard” linked here. I determined a method of detection based on utilizing this campaigns unique usage of hashes in a .txt for domain comparisons. Specifically there was many hashes that are reused within 28 different plugins I had originally manually identified through the Chrome Extension Website crx.dam.io. In order for my method of detection to work I had to download 550GB worth of data off the website in order to parse it automatically using a program to search zip files for the existence of one of the sample hashes from the .txt file.
It took quite awhile to find the best method of downloading this much data and this many links in a single instance. However, after multiple tries with different programs I determined the best method was wget2. This allowed me to download from the website in multiple threads. This sped up the download process from the website itself. What caused the other methods to fail was anything from not enough system memory, to crashes to seg faults within the programs.
However, once I did manage to get the data downloaded after multiple programs were tried to parse this much data(similar issues to above) I finally was able to search the data. A program named “FileSeek” was determined to be the best program based on my tests. It took a few days due to me having to store it on spin disk on a DAS but when it was complete I was surprised with the number of unique plugins that had been utilized in this campaign.
To view the raw data regarding this please visit the following google doc’s page which shows all of the details regarding each individual plugin:
https://docs.google.com/spreadsheets/d/1JI81z-5bELML2tUl_-MXHTq4STNli9T1XDKS4KnN-CY/edit?usp=sharing
Screenshot of Search Program and Some of the results Below:
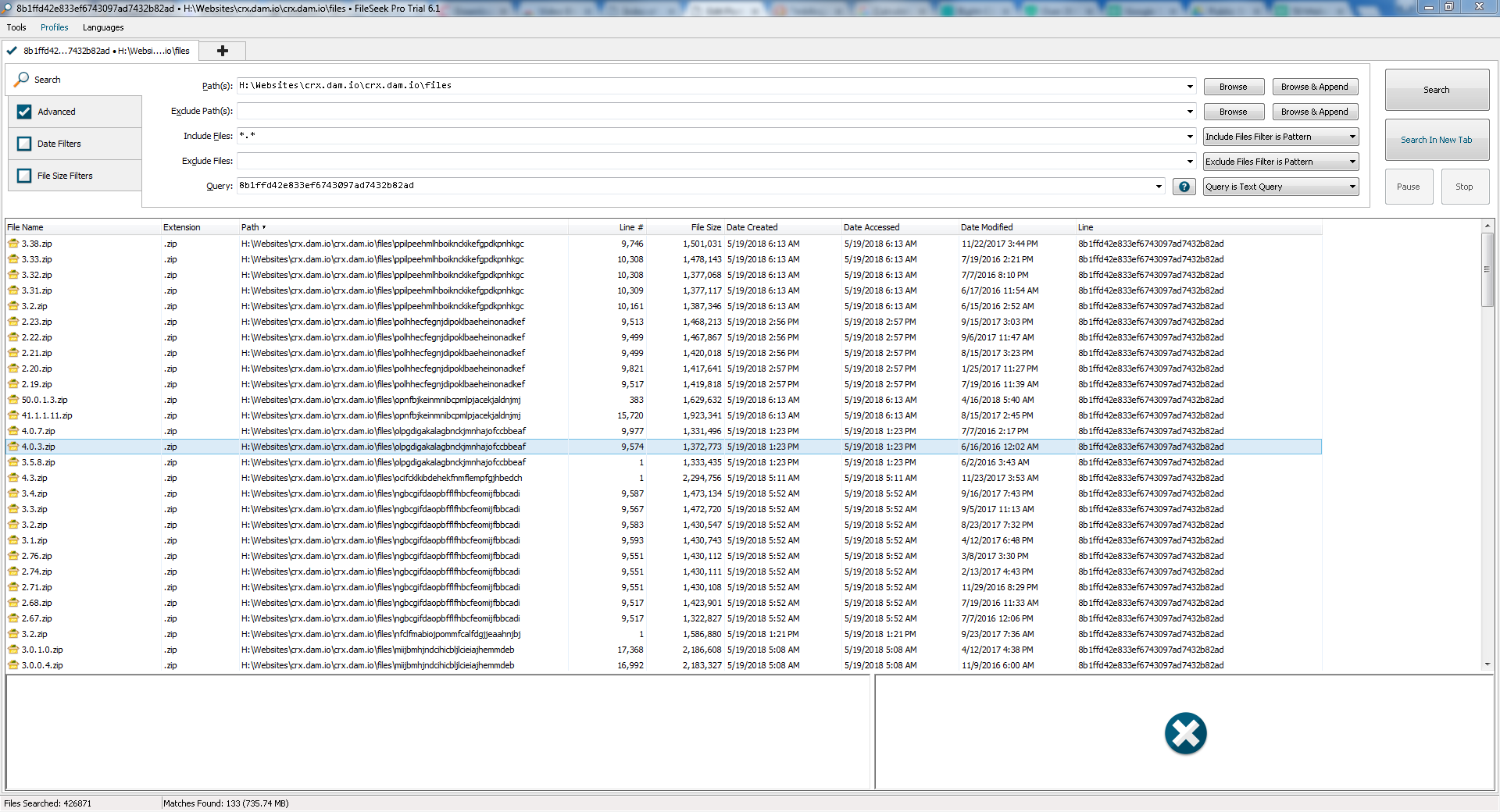
Being the skeptic I am I didn’t believe at first that there could have possibly been 50 malicious plugins or 133 malicious versions in this campaign. As such I started digging through the results and eventually verified that each and every result had not only the malicious code but the .txt file with the list of lookup hashes in the plugin itself.
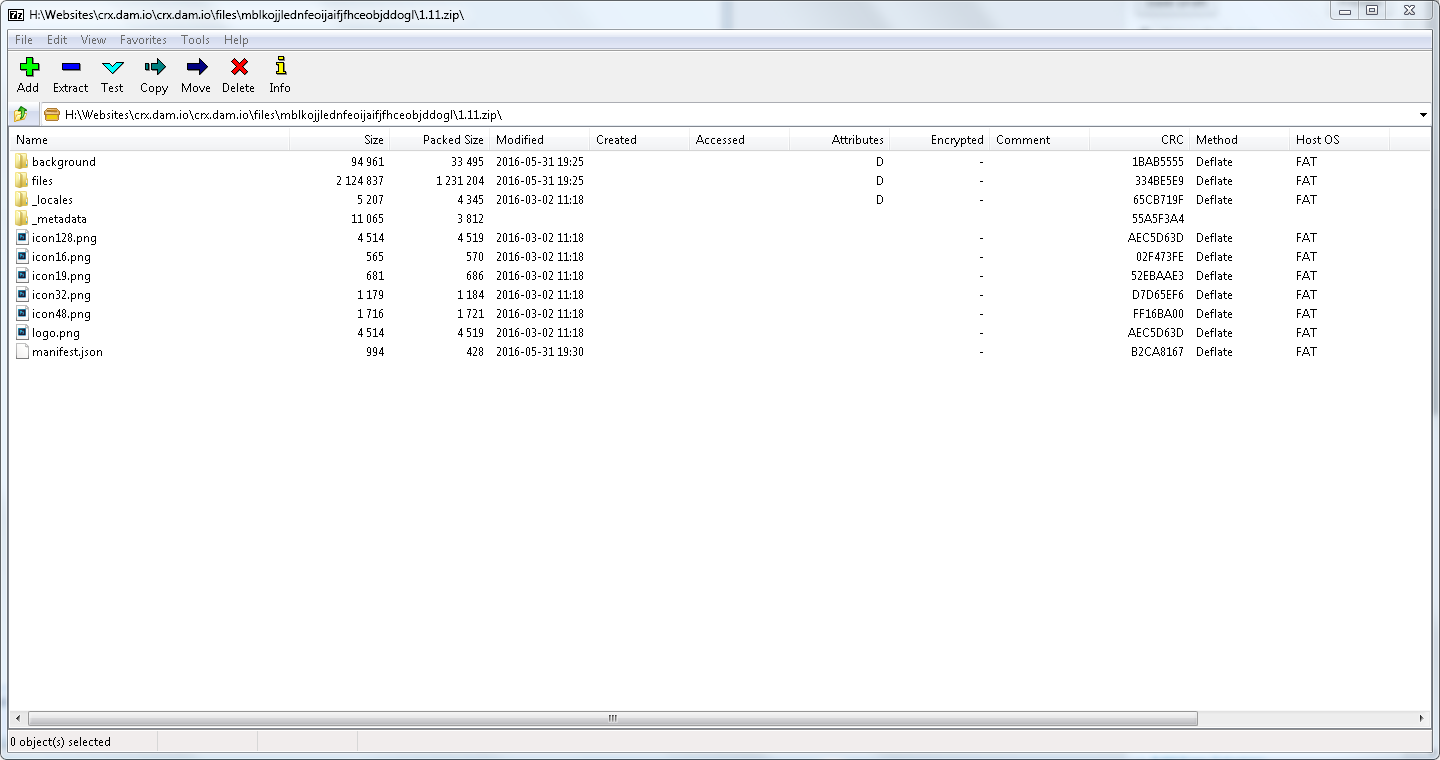
Screenshot of One of the .zip files:
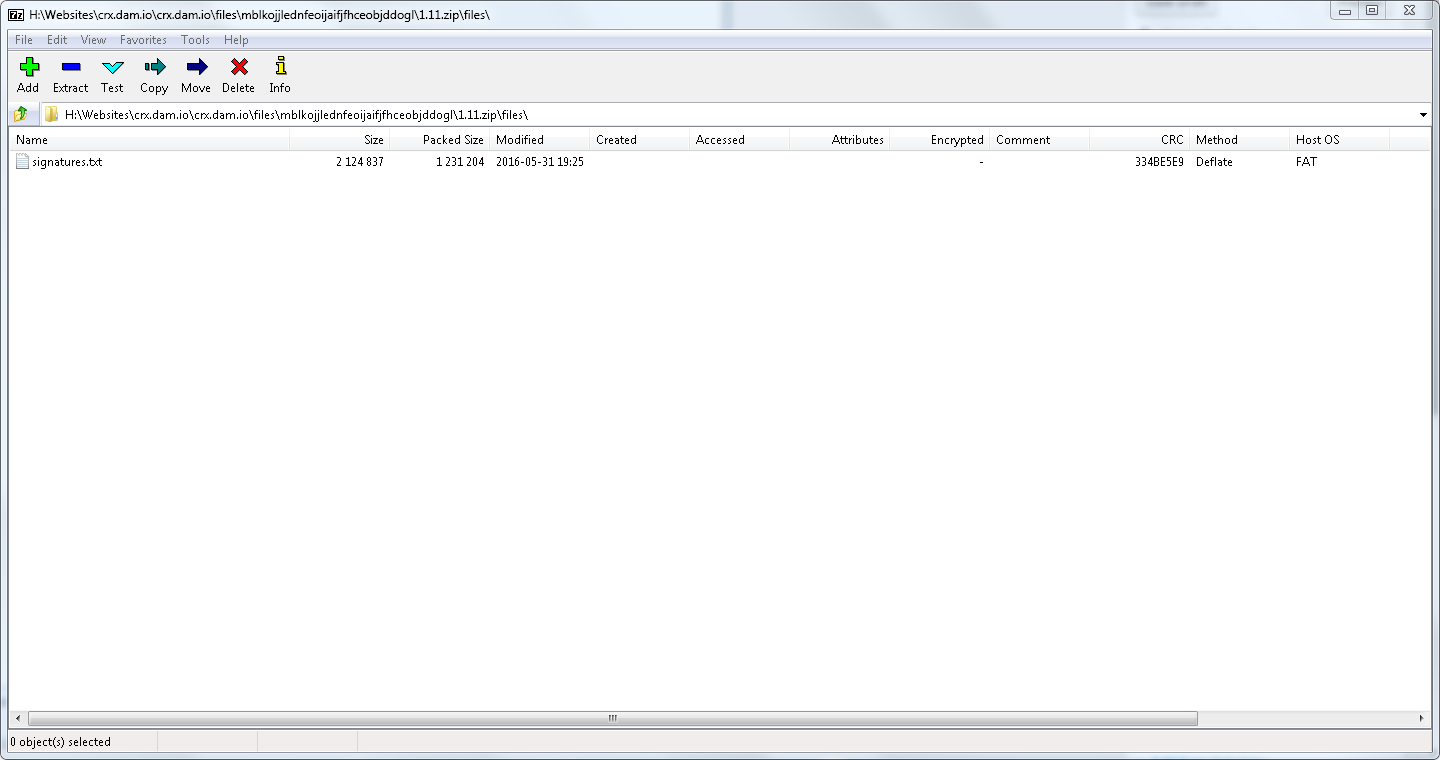
Screenshot showing one of the .txt files that are used for domain lookups(based on salted md5 hashes):
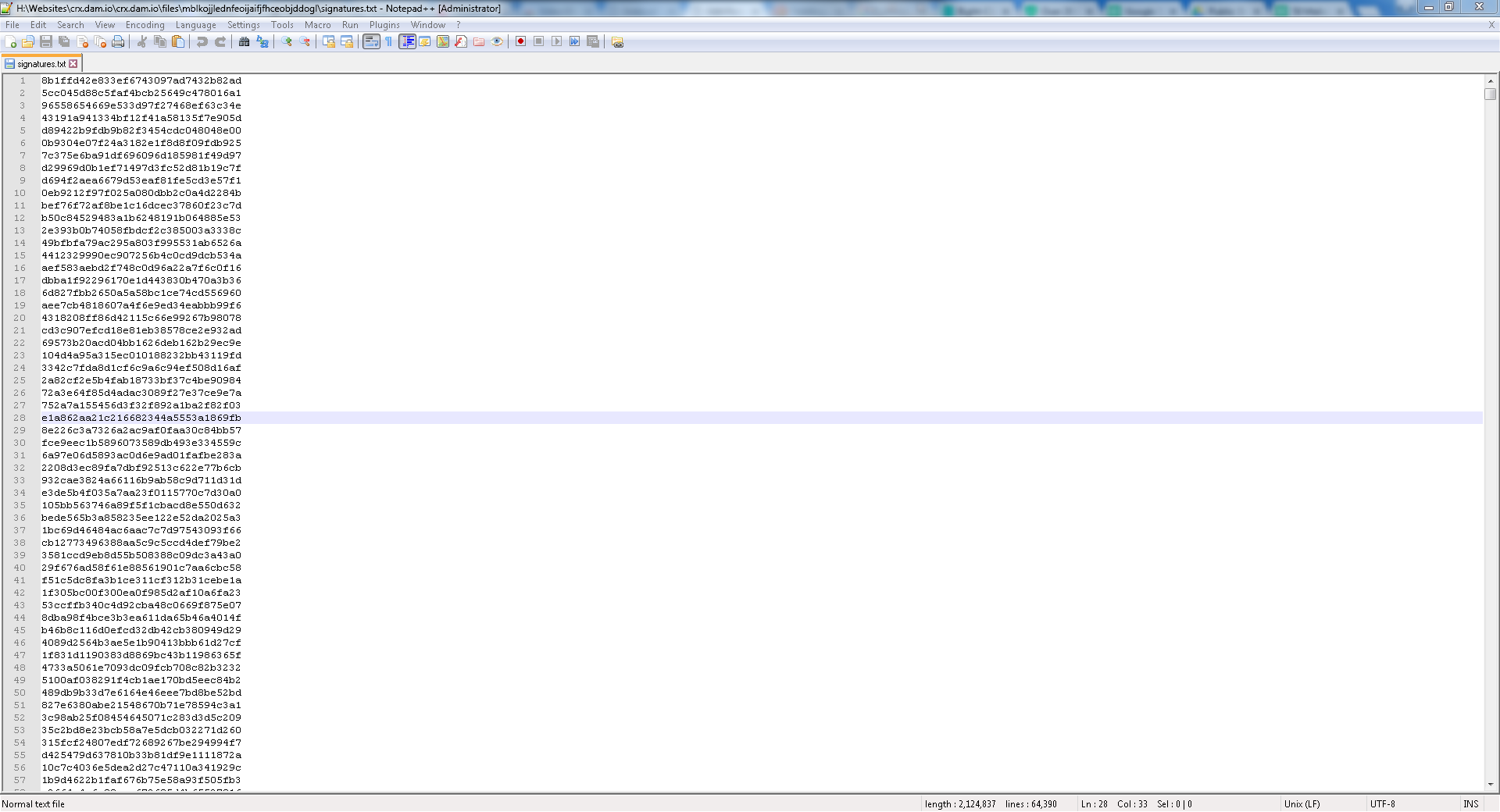
Screenshot of the inside of one of these .txt files used for the domain lookups:
Also,
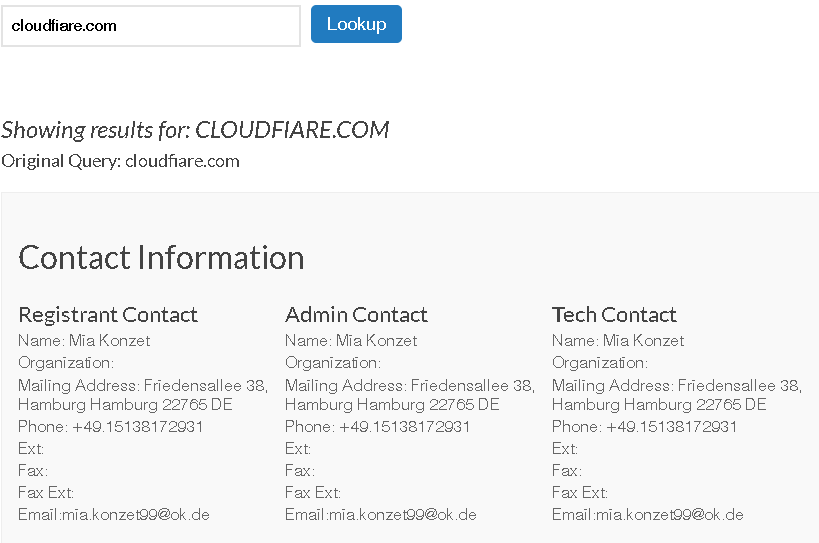
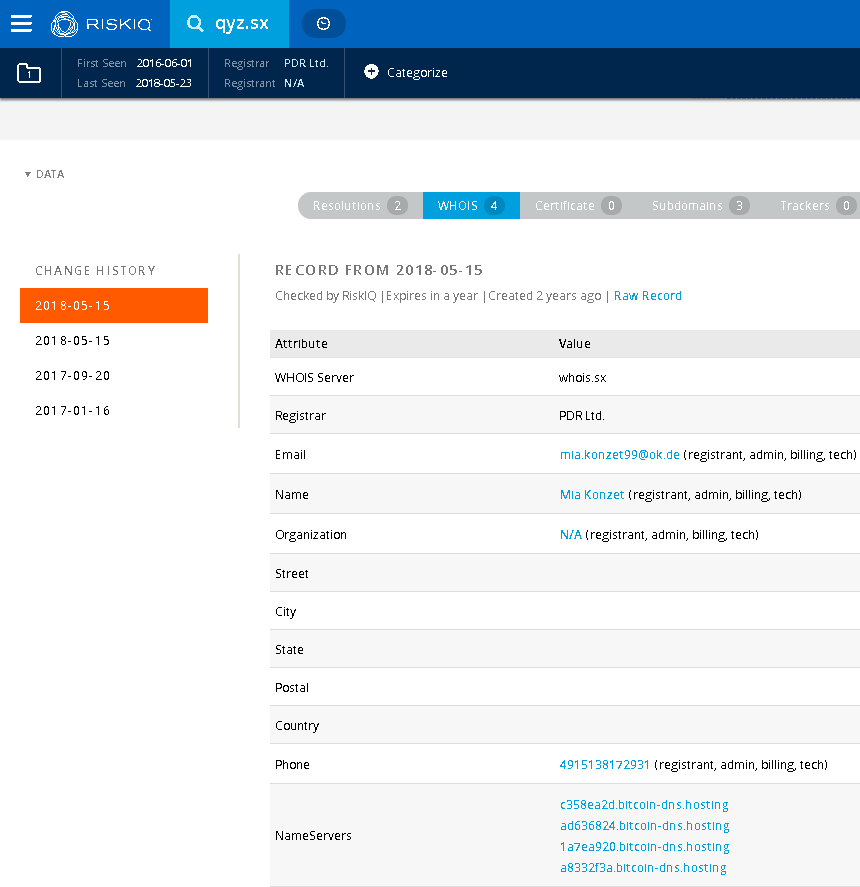
It is worth noting that OSINT on the domain itself pulled up some interesting results. While nothing conclusively links the domain registrant with any advance threat actor one of the domains the threat actor for these plugins registered did appear in the following ThreatConnect Report titled “What’s in a Name… Server?” as a “Additional Shady Domain”. I would rate the link to that threat intelligence report low to medium-low at best. It is interesting however that this report is specifically regarding the DNC breach and the OSINT available regarding APT 28/APT 29 and their TTPs during the breach itself.
Screenshot of whois information – cloudfiare[.]com:
Screenshot of whois information – Using Passivetotal Free for Lookup – g[.]qyz[.]sx:
My Personal Opinion as an InfoSec Analyst is that while it may have not been an APT it was much more advanced observed tactics than most the observed malicious plugins than I have seen publicly documented previously. Specifically, the use of Salted MD5 hashes of domains intended to be spied on by the plugin that never get decrypted, the use of legitimate plugin code that is only backdoored periodically and generally is not left with the current version backdoored in the play store(likely to avoid detection), use of Steganography, the code is split up in multiple places in the javascript and encoded so its not one big set of base64 encoded code, and the fact that when I ran the md5’s with their salts against the Alexa Top 1 Million it only decoded 19,000 of the domains being spied on.
List of 19,000 Decrypted Domains from MD5 List in .txt file being used for lookups to determine what domains to spy on:
https://drive.google.com/open?id=0B2lxMphiu9fcOXVwT0JvOGkyUkswWFU5NklobUZqay1yb1pN